

Instruction Set Architecture (ISA) The Instruction Set Architecture (ISA) is the part of the processor that is visible to the programmer or compiler writer.
The ISA serves as the boundary between software and hardware. We will briefly describe the instruction sets found in many of the microprocessors used today. The ISA of a processor can be described using 5 catagories: Operand Storage in the CPU Where are the operands kept other than in memory? Number of explicit named operands How many operands are named in a typical instruction. Operand location. Opcode. ISA[edit] Their specification and format are laid out in the instruction set architecture (ISA) of the processor in question (which may be a general CPU or a more specialized processing unit).
Apart from the opcode itself, an instruction normally also has one or more specifiers for operands (i.e. data) on which the operation should act, although some operations may have implicit operands, or none at all. There are instruction sets with nearly uniform fields for opcode and operand specifiers, as well as others (the x86 architecture for instance) with a more complicated, varied length structure. [1] Depending on architecture, the operands may be register values, values in the stack, other memory values, I/O ports, etc., specified and accessed using more or less complex addressing modes. The types of operations include arithmetics, data copying, logical operations, and program control, as well as special instructions (such as CPUID and others). Address space. In computing, an address space defines a range of discrete addresses, each of which may correspond to a network host, peripheral device, disk sector, a memory cell or other logical or physical entity.
Overview[edit] Address spaces are created by combining enough uniquely identified qualifiers to make an address unambiguous (within a particular address space). For a person's physical address, the address space would be a combination of locations, such as a neighborhood, town, city, or country. Some elements of an address space may be the same– but if any element in the address is different then addresses in said space will reference different entities. An example could be that there are multiple buildings at the same address of "32 Main Street" but in different towns, demonstrating that different towns have different, although similarly arranged, street address spaces. Examples[edit] Uses of addresses include, but are not limited to the following: Interrupt. Interrupt sources and processor handling Each interrupt has its own interrupt handler.
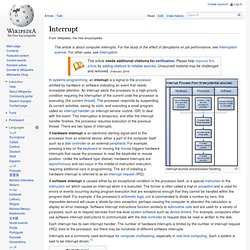
The number of hardware interrupts is limited by the number of interrupt request (IRQ) lines to the processor, but there may be hundreds of different software interrupts. Interrupts are a commonly used technique for computer multitasking, especially in real-time computing. Such a system is said to be interrupt-driven.[1] Overview[edit] If implemented in hardware, an interrupt controller circuit such as the IBM PC's Programmable Interrupt Controller (PIC) may be connected between the interrupting device and the processor's interrupt pin to multiplex several sources of interrupt onto the one or two CPU lines typically available. Interrupts can be categorized into these different types: Processors typically have an internal interrupt mask which allows software to ignore all external hardware interrupts while it is set.
An interrupt that does not meet these requirements is called an imprecise interrupt. RMS's gdb Tutorial: How do I use watchpoints? [contents] [usage] [execution] [stack] [breakpoints] [watchpoints] [advanced] Watchpoints are similar to breakpoints.

However, watchpoints are not set for functions or lines of code. Watchpoints are set on variables. When those variables are read or written, the watchpoint is triggered and program execution stops. It is difficult to understand watchpoint commands by themselves, so the following simple example program will be used in the command usage examples. #include <stdio.h> int main(int argc, char **argv) { int x = 30; int y = 10; x = y; return 0; } 5.1 How do I set a write watchpoint for a variable? Use the watch command. *NOTE* You may notice in the example below that the line of code printed doesn't match with the line that changes the variable x. (gdb) watch x Hardware watchpoint 4: x (gdb) c Continuing. 5.2 How do I set a read watchpoint for a variable? Use the rwatch command. (gdb) rwatch y Hardware read watchpoint 4: y (gdb) continue Continuing. Branch predictor. Figure 1: Example of 4-stage pipeline.
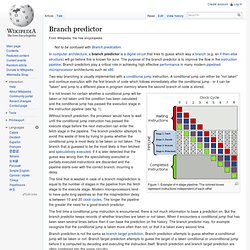
The colored boxes represent instructions independent of each other It is not known for certain whether a conditional jump will be taken or not taken until the condition has been calculated and the conditional jump has passed the execution stage in the instruction pipeline (see fig. 1). Without branch prediction, the processor would have to wait until the conditional jump instruction has passed the execute stage before the next instruction can enter the fetch stage in the pipeline. The branch predictor attempts to avoid this waste of time by trying to guess whether the conditional jump is most likely to be taken or not taken.